Last year in September I wrote an
article for Hakin9 on how to detect, identify and of course disinfect a machine from malware.
I've decided to publish it on my blog as well, you can also download it from the following links in PDF format:
http://www.mediafire.com/?gz7qic8h7xcgysthttp://www.mijnbestand.nl/Bestand-KGJYA43TA3BP.pdf (mirror)
Here's the article:
Basic Malware Cleaning
Malware is common nowadays. Each day, machines get infected with viruses, spyware, Trojans, keyloggers, rogueware, ransomware, rootkits, … The list continues with more advanced malware like Conficker, Duqu, Stuxnet, Flame, …
The malware scenario on itself has also drastically changed. Where in the past, malware was created for showing off your skills or gaining your 15 minutes of fame (remember LoveLetter?), it is now almost solely used for the purpose of making money.
If you are reading this article, you have already helped someone getting rid of malware infestations, or you at least have an interest in the basics on how to clean malware from an infected machine.
What you will learn...
- Identifying malicious processes, terminating these processes and how to properly prevent them from running
- Identifying malicious startup entries and system modifications
- Identifying related malicious files, meaning droppers and payload
- Identifying the malware source and effectively tackling it
What you should know...
- Basic computer knowledge and common sense
- Use a proper environment for testing purposes
About the author
The author has been working as a technical support engineer in the antivirus industry for several years and is also involved in performing malware research and malware analysis, intended primarily for improving his own skills and raising awareness amongst every computer user, whether it would be home or business users. You can follow him on Twitter: @bartblaze
Introduction
Before we begin, I’d like to make clear that if you want to test your skills after reading this article or want to test malware in general, you should set up a proper testing environment. Make sure you are using a Virtual Machine if testing on your own machine, or create a machine for the sole use of testing malware and antimalware tools. In either case, it’s a good idea to use a separate network or use a DMZ should you have one. Personally I recommend having the machine connected to the internet, so the malware can do its evil work to its maximum potential and you will be able to carefully study and dissect its workings completely. I’ve made a post on my blog as well on how to build your own malware analysis lab: http://bartblaze.blogspot.com/2013/06/basics-for-malware-analysis-lab.html
More tips can be found in the section On The Web in the last paragraphs of this article.
In the next paragraphs, we will see three possible malware scenarios:
- Rogueware
- Trojan horse
- Rootkit
For each malware scenario or case study, a sample was executed and the machine was consequently rebooted to view the malware’s effects. Each case study will be outlined with the necessary tools and steps to take on how to completely eradicate the above infection types. Note that after performing manual clean-up, it is advised to perform a scan with an (preferably) online antimalware or antivirus product. Most antivirus companies offer a free online scan and automatic removal.
We will be making use of the following tools:
- Autoruns
- GMER
- Process Explorer
- RootkitRevealer
- Rootkit Unhooker
First case study - Rogueware
Rogueware is probably one of the most known types of malware nowadays. The reason is simple: when one gets infected with rogueware, annoying pop-ups will appear all over the screen, urging to buy their precious Antivirus, which has found enough infections on your machine to completely toast it – if they were real. Rogueware is simply blatant enough to appear fully on your screen, whereas most other types of malware will (try to) work silently in the background.
In this first case study we will only make use of the tools Process Explorer and Autoruns, both created by Sysinternals.
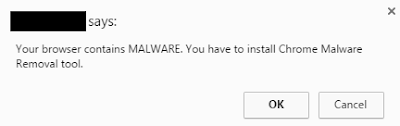
After running our first sample and rebooting the machine, we receive several messages that the machine is infected and we should take immediate action. A screenshot of this specific rogueware:
Figure 1. Rogueware called ‘Live Security Platinum’ running on our machine
Let’s start Process Explorer and see what’s running!
Figure 2. Process responsible for Live Security Platinum
What can you make of this screenshot? There are indicators this is indeed malware:
- Random filename
- No file description
- No company name
Explaining why there is a random filename:
trying to evade specific antimalware tools which focus only on names the malware uses – for example, I remember a specific rogueware family from back in 2009 that always placed the same DLL in the System32 folder: win32extension.dll
Tip: If you’re in doubt whether a process is malicious, simply right-click it in Process Explorer and select Search Online...
Most of the times, Google will have a history of this filename. If the search is turning up zero results, it’s an extra confirmation that it concerns a malicious process.
Explaining why there is no file description or company name is simple: in earlier days – the days of Windows XP to be exact – the basic Task Manager did not display any file description or company name. So basically, there was no use in including it since it wasn’t displayed anyway. In Windows Vista, Windows 7 and soon Windows 8 Task Manager is improved.
This malware hides in %appdata%, which is a system variable for the Application Data folder of the currently logged on user. What else can we deduct from this screenshot? The rogueware uses a Microsoft icon, thus trying to trick the user to indicate it’s nothing malicious. An effective trick indeed, but considering the previous factors, we can be sure this is a malicious process which needs to be terminated.
A useful setting in Process Explorer is through Options > Verify Image Signatures. With this option, you’ll be able to quickly determine if a file claiming to be from Microsoft is indeed so or not. Note that these may be forged.
There are three color codes important for us:
- Green– new process
- Red – killed process
- Purple– process with images that are packed. Intention: hiding strings, evading antivirus detections
By right-clicking the process and choosing Properties, we can gather more intelligence about the file. A short overview of the tabs useful for our malware identification:
- Image– image file properties
- Strings– strings loaded into the image or memory
Figure 3. Image Tab details
Thanks to the Image tab, we are able to view the file location, any command line arguments there may be, but also if the file has a valid Image Signature and the current directory from where the file is executed.
Moving over to the Stringstab, where we may find interesting information about the file and its behavior. An example:
Figure 4. Payform.html, which is the rogueware’s own webpage to order its ‘product’
Let’s close this and start with the cleaning of this type of malware.
First step is killing the rogueware by right-clicking the process in Process Explorer and choosing Kill Process. The rogueware will disappear like snow in the sun. Note that some rogueware is protecting or guarding each other’s process, so it’s possible you will have to Suspend a process first before killing its guardian. Afterwards you can kill the first process and the rogueware will not re-appear again.
Second step is of course disabling the rogueware from starting up with Windows. In order to do so, we will be using Autoruns:
Figure 5. Autoruns Logon tab view
Navigate to the Logon tab and choose to delete it. Click Yes to confirm. Close Autoruns. If you are unsure about a Logon entry, simply untick the checkbox first instead of deleting it.
A trick that is often utilized by malware authors is to hijack several antivirus processes to, for example, svchost.exe or to their own malicious program. They do this to prevent antivirus software from running and making sure their malicious program will be executed. Sometimes, Task Manager, Regedit, the Command Prompt(CMD) and other tools are hijacked as well. I’m sure you have encountered before that you were unable to run any of these built-in Windows features. The reason is Image Hijacks.
We will now be using the same trick against them, by creating our own Image Hijack or, as Microsoft calls it: Image File Execution Options. To do so, we will use Regedit:
Figure 6. Image Hijacks can be added under: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
In order to add an Image Hijack, right-click on the Image File Execution Options key and select to create a new Key. This key must be the exact same name as the malware name. In our first case study, this means: 529C50D8212C2CDD6A42F365D151FC4E.exe
We subsequently create a new StringValue under this key with Value Name:Debuggerand Value Data: svchost.exe. Now, even when the rogueware is still on the system, it cannot start since it will be forced to start svchost instead.
You can also do this faster by using the following small piece of code and running it by clicking on Start> Run and pasting it in the message box. Replace XXX.exe by the name of the malware:
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\XXX.exe" /v Debugger /d "svchost.exe" /f
In our first case study, for the ‘Live Security Platinum’rogueware, this would be:
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\529C50D8212C2CDD6A42F365D151FC4E.exe" /v Debugger /d "svchost.exe" /f
Tip: in Autoruns there’s a useful tab called Image Hijacks which will display any present modifications to this key:
Figure 7. Check if there are any Image Hijacks present
Have you completed all these steps, reboot the machine. If nothing seems to pop up or alarm you, you can visit the folder where the rogueware resides and delete the malicious file. Note that you might have to enable Hidden files, folders or drives, and to unhide Protected Operating System files. You can do this via Windows Explorer:
- For Windows XP: Tools > Folder Options > View
- For Windows Vista and Windows 7: Organize > Folder and Search Options > View
This concludes our first case study. Be sure to remember it, as we will be using the same tools for our next malware family:
a Trojan horse.
Second case study – Trojan horse
Trojan horses or Trojans are typically data stealers and can copy themselves on your machine. They may also turn your machine into a zombie, which is basically a computer part of a botnet.
Trojans often disguise themselves as legitimate programs; for example an upgrade of Adobe Flash Player, a crack or key generator for a game or Microsoft Office and many more.
After executing our sample and rebooting the machine, we don’t see anything malicious in Process Explorer. Actually, we are seeing something strange. A Firefox instance was running even though we didn’t start Firefox. When starting Firefox manually, it gets loaded under Explorer. In this case, it was not loaded under Explorer, but started as a separate process:
Figure 8. Malicious Firefox process loaded. As you can see, svchosts.exe is injected into Firefox
The Trojan has loaded a malicious version of a Firefox process, to effectively hide itself from users. After all, who would suspect a Firefox process to be malicious? You can search for Handles or DLLs via the menu Find. Svchosts.exe is the Trojan on itself, which we will see below. Note: for this reason, the Trojan has rootkit capabilities, which we will discuss in the next case study.
If we verify any system modifications with Autoruns, there are two new entries added in the Logontab:
Figure 9. Two new entries in the Logon tab of Autoruns. We will now discuss some characteristics
In Figure 9 there are two entries highlighted: one under HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit, while the other one can be found under HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
The Trojan has attached itself to the Userinit value, which will ensure that it starts right after a user logs in to Windows. It has also placed an entry in the Run key, as an extra check to start up with Windows.
If we take a look at the Trojan’s file information:
Figure 10. Trojan’s file information
There are a few things that should get your alarm bells ringing:
- The file is only 188 kB
--> files with a small size are more likely to contain malware - The filename is svchosts.exe and resides in C:\Windows--> malware imitating legit Microsoftfiles is not uncommon
--> the legit file is named svchost.exeand resides in C:\Windows\system32--> most, but not all, malware hides in C:\Windows or C:\Windows\system32 - The file description reads “deine mutter”--> which is German for “your mother” and is considered an insult in some countries
- The icon of a microphone is used into tricking you this might be legit software--> voice or audio recording software for example
Let’s move on and start disinfecting the machine step by step. First step is to Kill the malicious Firefox process with Process Explorer.
Next, open up Regedit and navigate to the following key: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Figure 11. Hijacked Userinit value
Restore the default Userinit value by double-clicking on the value and entering as Value data (this is the default Value data for Userinit):
c:\windows\system32\userinit.exe
Open Autoruns again or should you not have closed it, refresh. You will see the first entry has disappeared. Now simply delete the other value.
Tip: did you know you can easily access the Registry via Autoruns? Right-click an entry, select Jump To…and you will be taken there instantly. Very useful in cases where the Userinit, Winlogon or Shell Valuekeys are hijacked or altered.
At this point, reboot the machine and verify with Process Explorerthat there aren’t any malicious processes still present, or a malicious Firefox process. Verify with Autoruns that all startup entries are removed. Navigate to the folder where the malware hides and delete the responsible file(s).
This concludes our second case study. In the next case study we will see how to handle a rootkit infection.
Third case study - Rootkit
Rootkits are a type of malware apart. Rootkits are software which can hide processes, files & folders, drivers, registry keys and much more from the Operating System, antivirus software and many security tools. Rootkits can also be used to gain and retain administrator privileges on a machine.
Typically, you can divide rootkits into two categories or types:
- User mode or user land rootkits
- Kernel mode or kernel land rootkits
Figure 12. Figure of protection rings. Rings are mechanisms to protect data and functionality from
faults and malicious behavior. (Image source: Wikipedia)
User mode rootkits: operate in Ring 3, together with user applications
Kernel mode rootkits: operate in Ring 0, with the highest Operating System privileges
Rootkits can perform many tasks, besides hiding themselves, they can also disable antivirus components, perform DLL injection (inject and run code in the address space of another process), hide other malware, download additional malware, provide an attacker access to the machine, turn the machine into a zombie, …. You get the point.
In this case study, we will see the infamous TDL3 rootkit (which is a ring 0 rootkit), more specifically the “4DW4R3” rootkit. It was dubbed the 4DW4R3 rootkit because of the strings found in the associated DLLs. (associated files for this malware also start with 4DW4R3 and attached 10 random letters after it, for example: 4DW4R3vDqMXSvfxR.dll)
After executing the sample, it gets deleted immediately. Let’s reboot the machine at this point and document our findings.
Firing up Process Explorer and Autoruns still works normally, but there doesn’t seem to be anything suspicious. In this case, we will need to run some more specialized tools in order to uncover the rootkit’s modifications to the system.
When encountering a rootkit infection, it is recommended to run at least three different anti-rootkit tools. Why?
- Anti-rootkits can produce false positives
- The rootkit may have used hooking to prevent certain anti-rootkit tools from running or
even displaying incorrect results
The first anti-rootkit tool we will be using is RootkitRevealer, another Sysinternals tool:
Figure 13. RootkitRevealer found four files hidden from the Windows API. This means you won’t be able to view them, not even
when having the option on to view hidden files and folders, or protected operating system files
Note that we will only focus on the highlighted changes for now. The others are also from rootkit modifications, where it is denying access on certain registry keys for RootkitRevealer.
Now that we have uncovered associated files from the rootkit, we can use Process Explorer again to verify if there has been any DLL injection. In our second case study, we have already briefly seen this occurrence.
Figure 14. Through the menu Find > Find handle or DLL… We discover that 4DW4R3vDqMXSvfxR.dll is injected into svchost.exe
Besides injecting into svchost.exe, the rootkit will also (attempt to) inject itself in newly created processes, for example firefox.exe.
Result is you will be redirected to a shady search engine whenever you are trying to search something on Google, Yahoo or other search engines. This can be verified by opening the 4DW4R3vDqMXSvfxR.dllfile in Process Explorer and selecting the Strings tab
(be sure to select Memory):
Figure 15. Search results on Bing, Google, Yahoo, AOL,… Will all be redirected to another (malicious) search engine
When using Rootkit Unhooker, it notifies us of Possible Rootkit Activity. When reading the log, we see the following lines:
==============================================
Stealth
Unknown page with executable code
Address: 0xF889C8BB
Size: 1861
This indicates there’s something stealth, which may be malicious, at address space F889C8BB. The code at this address space is probably used to prevent the scanning of registry keys by certain anti-rootkit tools, as was the case with RootkitRevealer.
When using GMER, it starts a scan of the system right away and will state whether or not there’s an infection:
Figure 16. The 4DW4R3 rootkit has also been discovered by GMER
Let’s review what GMER has found as system modifications:
Code F889BEB5 ZwCallbackReturn
Code F889B979 ZwEnumerateKey
Code F889B96F ZwSaveKey
Code F889B974 ZwSaveKeyEx
Code F889BBD2 IofCompleteRequest
ZwCallbackReturn: ensure communication between user mode malware components and the kernel mode rootkit
ZwEnumerateKey: hide registry keys, prevent anti-rootkits from scanning the registry
ZwSaveKey & ZwSaveKeyEx: prevent some anti-rootkits from scanning the registry or detecting mischief
IofCompleteRequest: hide and protect rootkit files
Let’s review what GMER has found as service modifications:
· Service C:\WINDOWS\system32\drivers\4DW4R3nKkNtexUqD.sys (*** hidden *** ) [SYSTEM] 4DW4R3 <-- rootkit="">-->
It is obvious by now the machine is infected with a rootkit. We will be using GMER to fully disinfect the machine. Right-click the service and choose Delete Service. If you receive an error, choose Disable Service. Reboot the machine.
Now that the service is deleted (or disabled) we are able to view the files the rootkit has placed. Simply delete them and reboot:
Figure 17. The rootkit’s associated DLLs and drivers
This concludes our third case study. In the next paragraphs you’ll be able to find additional information on how to handle a malware incident.
Signals of infection
In most cases, it’s pretty obvious when facing an infection like rogueware or ransomware: pop-ups and annoying messages all over the screen.There are other symptoms which may not always seem originating from malware:
- Failing of Windows Firewall, Windows Security Center warnings. Microsoft Update malfunctioning.
- Not being able to execute antimalware tools. Not being able to visit websites from antivirus vendors.
- Redirections taking place in your browser to shady search engines.
- Severe slowdown of the machine. More bandwidth usage than usual.
- Suddenly finding software on your machine you never installed or never gave permission to.
These are called Potentially Unwanted Programs (PUP) or Adware. - Unexpected Blue Screens (BSOD). This might be due to a badly written rootkit for example.
- Unexpected errors or malfunctioning of antivirus and antimalware programs.
General tips and tricks
In this section I’ll add some extra tips and tricks for problems you might encounter during the disinfection process:
- If a tool is refusing to run, try renaming it to explorer.exeor svchost.exe. Some rogueware families will block all applications, but will allow system processes to run.
- If a tool is refusing to run, and you already tried above trick, try renaming to SomeName.com. It’s possible all EXEfiles are disallowed from running. There’s a tool called exeHelper which will restore the default values for PE (executable) files.
- Another useful tip is trying to boot the machine in Safe Mode. Some malware will only place a value in HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run, which is ignored when booting in Safe Mode.
Note that malware X won’t do much in Safe Mode, but can actually still be downloading additional malware if you decide to boot in Safe Mode with Networking.
- Rootkits can interrupt the execution of several anti-malware tools, where even above tricks won’t be able to help. In that case, you should try fixing the permissions of those tools. A very useful tool for this is Inherit. Just drag and drop the tool or program you want to execute on Inherit. Wait for the message box “OK” to pop up and you should be able to run it.
- Also in case of a rootkit or any other malware infection, it is advisable to change your most important passwords after fully cleaning the machine. Remember that when having encountered a rootkit infection and cleaning the machine, it is possible there are still infection leftovers. In case of doubt, reinstall Windows completely. In case of a bootkit, which infects the MBR, you need to boot the machine from the Windows installation CD, choose the Recovery Console, and type the command fixmbr in the command prompt. Press Enter and the MBR or Master Boot Recordwill rebuild.
- In some cases, the machine is infected so badly that it’s almost unworkable to run any tool. It’s also possible you cannot boot into Windows anymore. In such cases, you can use a boot CD or safe CD from an antivirus vendor. An alternative is the Sardu Multiboot CD or DVD and USB creator, which combines several antivirus rescue CDs. Or you can completely reinstall the machine. Tip: take regular back-ups of important files and folders!
Prevention tips and tricks
I’m guessing most of you already know how to protect yourself against mischief, though I’ll repeat some general tips once again. Repetition is key. Some do’s and don’ts:
Do install an antivirus program – yes, you never use antivirus and you’ve never been infected before. Still, using antivirus reduces the chance even more.
Do uninstall applications you don’t need – examples are Java and Adobe. If you do need them, update them frequently.
Do uninstall browser extensions you don’t need. If you do need them, check for updates frequently.
Do your updates. This includes Windows updates, antivirus updates, browser updates and any other software you may be using.
Do use layered protection if possible – Firewall at hardware level (router), HIPS, antivirus, antimalware …
Don't open email attachments from unknown senders - ever.
Don’t click on everything on the internet. Meaning: use common sense when browsing the web.
Don’t trust everything on the internet. If it looks too good to be true, it probably is!
Don’t fill in your personal information or email address on random websites.
Don't use the same password for each and every website! Implement proper password security.
Don’t panic if you suspect you’ve been infected. Read the tips below on what to do if you are.
Help! I’m infected!
What could be the best procedure if you suspect to be infected? Suggested model:
· Stay calm, don’t panic. Disconnect yourself from the network.
· Identify and kill malicious processes.
· Identify and delete malicious autorun entries.
· Reboot and repeat the previous steps.
· Delete associated files and folders.
· Run a full scan with your installed antivirus product.
· If disinfection is applied successfully, connect to the network again. If possible, connect to a separate network first to verify everything is indeed back to normal or not. Perform an online scan with another antivirus product than the one you have installed.
If you’re in a corporate network, what could be the best procedure if you suspect to be infected? Suggested model:
· Stay calm, don’t panic. Disconnect yourself from the network & contact your network administrator.
· Write down useful information:
o What were you doing at the time? Did you notice anything special? What was the time and date anyway?
o Why do you believe your machine is infected? Which steps did you take already, if any? Did your antivirus prompt?
o Inform your co-workers you’re going for a coffee break.
Summary
This concludes our three case studies – rogueware, Trojan Horse and rootkit. I do hope that you have enjoyed reading the article and going carefully through each step.
We have seen three different case studies as described above, but it is totally not uncommon to have all three types of malware on the same machine. For example, certain families of rogueware have been seen to dropthe infamous TDL4 rootkit variant. Goal is to ensure the persistence of the payload on the machine. Therefore, it is advised to always use an anti-rootkit as well.
Remember that some malware is more advanced than others, and it might take you some time to fully disinfect a machine. Sometimes it’s easier, quicker and cleaner to perform a reinstallation of the operating system. If you’re ever stuck, there are many forums out there specifically for helping you in cleaning malware off an infected computer.
As quickly as malware is evolving, so are the people who are constantly battling them – whether this would be antivirus companies, independent malware or security research folks, agencies and governments… Join our cause in making this world a malware-free environment and educate everyone around you, each day.
Should you have any further questions, comments or remarks, I am always available for feedback. You can contact me via Twitter:
@bartblaze.
Glossary
Address space – in this context, memory address of a process.
Botnet – a group of computers infected with malware and controlled by the so called bot herder. Botnets can be used to launch DDoS attacks, send spam …
Dropper – a dropper is a program that installs or downloads additional malware on a system.
LoveLetter – also known as ILOVEYOU worm – spread mostly via email, infected millions of machines.
Master Boot Record – first 512 bytes at the first sector of a hard drive.
Payload – modifications or damage done by malware.
Zombie – computer infected with malware and possibly compromised by a hacker. Zombies are typically part of a botnet.